Setting up captive portal (Wifi) on raspi
Using nodogsplash.
First set up the raspi as a WiFi access point (AP)
Following these installation instructions and referencing the official Pi directions.
Install the software packages:
sudo apt update
sudo apt -y upgrade
sudo apt install -y hostapd dnsmasq
sudo systemctl unmask hostapd
sudo systemctl enable hostapd
sudo DEBIAN_FRONTEND=noninteractive apt install -y netfilter-persistent iptables-persistent
and then rebooting
sudo reboot
Add the following code to the file /etc/dhcpcd.conf
cat <<EOF | sudo tee -a /etc/dhcpcd.conf
interface wlan0
static ip_address=192.168.4.1/24
nohook wpa_supplicant
EOF
and likewise for /etc/sysctl.d/routed-ap.conf
cat <<EOF | sudo tee -a /etc/sysctl.d/routed-ap.conf
# Enable IPv4 routing
net.ipv4.ip_forward=1
EOF
and same for /etc/dnsmasq.conf
cat <<EOF | sudo tee -a /etc/dnsmasq.conf
interface=wlan0 # Listening interface
dhcp-range=10.0.0.2,10.0.0.12,255.255.255.0,24h
# Pool of IP addresses served via DHCP
domain=wlan # Local wireless DNS domain
address=/gw.wlan/10.0.0.1
# Alias for this router
EOF
and also for /etc/hostapd/hostapd.conf
cat <<EOF | sudo tee -a /etc/hostapd/hostapd.conf
country_code=AU
interface=wlan0
ssid=NoDoggySplashy
hw_mode=g
channel=11
#ssid=NoDoggySplashy5G
#hw_mode=a
#channel=48
macaddr_acl=0
auth_algs=1
ignore_broadcast_ssid=0
#wpa=2
#wpa_passphrase=qwertyuiop
#wpa_key_mgmt=WPA-PSK
#wpa_pairwise=TKIP
#rsn_pairwise=CCMP
EOF
sudo raspi-config nonint do_wifi_country AU
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
sudo netfilter-persistent save
sudo reboot
The AP should now be visible to other devices with WiFi enabled.
Captive portal nodogsplash
For the nodogsplash installation, install requirements, obtain software and compile it as follows:
sudo apt-get update
sudo apt install git libmicrohttpd-dev build-essential git libmicrohttpd-dev build-essential -y
cd ~
git clone https://github.com/nodogsplash/nodogsplash.git
cd nodogsplash
make
sudo make install
Make sure the following settings are correct in /etc/nodogsplash/nodogsplash.conf
GatewayInterface wlan0
GatewayAddress 192.168.1.237
Set the the captive portal to start automagically and start it now:
sudo cp ~/nodogsplash/debian/nodogsplash.service /lib/systemd/system/
sudo systemctl enable nodogsplash.service
sudo systemctl start nodogsplash.service
And checking the status
sudo systemctl status nodogsplash.service
should show something like
● nodogsplash.service - NoDogSplash Captive Portal
Loaded: loaded (/lib/systemd/system/nodogsplash.service; enabled; vendor preset: enabled)
Active: active (running) since Tue 2023-03-14 04:27:45 GMT; 12min ago
Process: 673 ExecStart=/usr/bin/nodogsplash $OPTIONS (code=exited, status=0/SUCCESS)
Main PID: 678 (nodogsplash)
Tasks: 4 (limit: 2059)
CGroup: /system.slice/nodogsplash.service
└─678 /usr/bin/nodogsplash
Mar 14 04:27:44 raspi303 systemd[1]: Starting NoDogSplash Captive Portal...
Mar 14 04:27:45 raspi303 nodogsplash[673]: [5][Tue Mar 14 04:27:45 2023][673](src/main.c:359) Starting as daemon, forking to background
Mar 14 04:27:45 raspi303 nodogsplash[673]: [5][Tue Mar 14 04:27:45 2023][678](src/main.c:273) Detected gateway wlan0 at 192.168.1.237 (b8:27:eb:a6:b5:f1)
Mar 14 04:27:45 raspi303 nodogsplash[673]: [5][Tue Mar 14 04:27:45 2023][678](src/main.c:289) Created web server on 192.168.1.237:2050
Mar 14 04:27:45 raspi303 systemd[1]: Started NoDogSplash Captive Portal.
Mar 14 04:27:45 raspi303 nodogsplash[673]: [5][Tue Mar 14 04:27:45 2023][678](src/fw_iptables.c:380) Initializing firewall rules
Mar 14 04:28:31 raspi303 nodogsplash[673]: [5][Tue Mar 14 04:28:31 2023][678](src/client_list.c:139) Adding 10.0.0.3 52:1d:b8:2e:05:de token 7ef0af99 to client list
Mar 14 04:38:47 raspi303 nodogsplash[673]: [5][Tue Mar 14 04:38:47 2023][678](src/auth.c:188) Timeout preauthenticated idle user: 10.0.0.3 52:1d:b8:2e:05:de, inactive: 616s, in: 0kB, out: 0kB
Mar 14 04:38:47 raspi303 nodogsplash[673]: [5][Tue Mar 14 04:38:47 2023][678](src/client_list.c:370) Deleting 10.0.0.3 52:1d:b8:2e:05:de token 7ef0af99 from client list
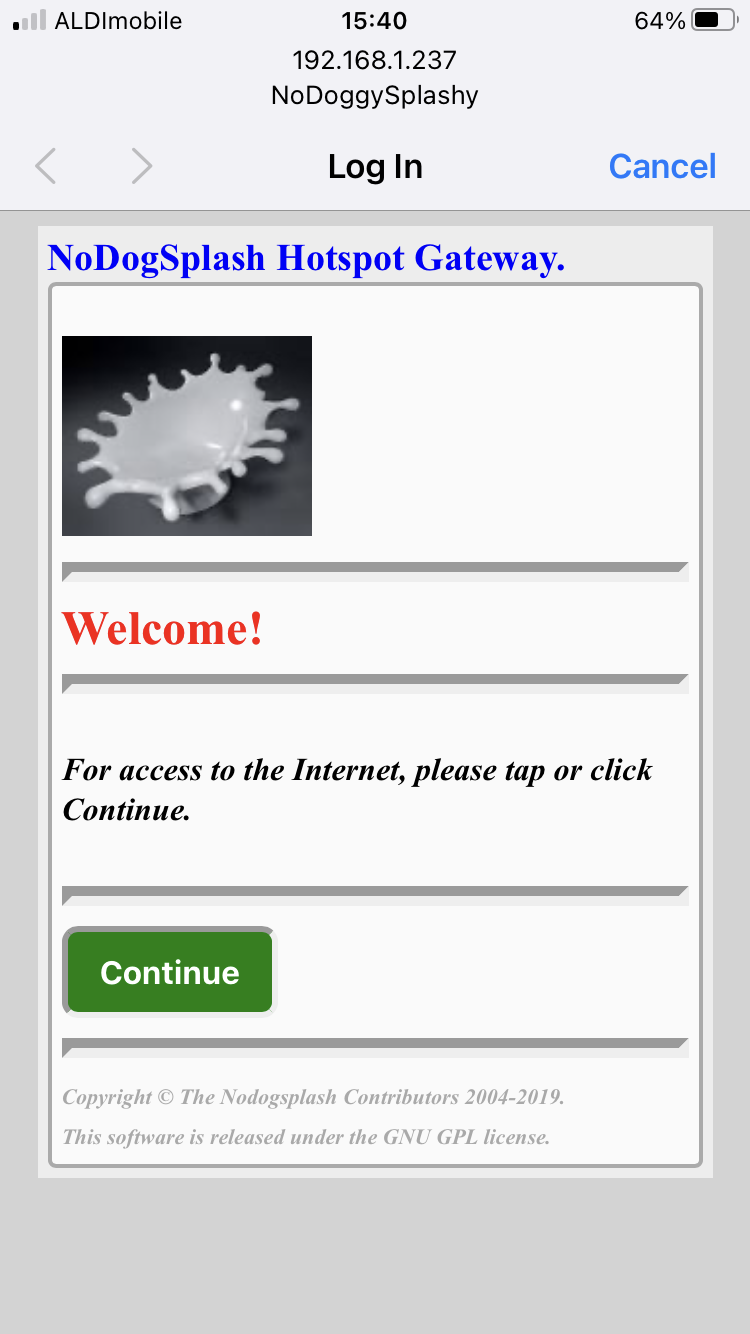
Accessing the AP shows the following